Tech Talk
 | Catalog Basics – Catalog Components |
 | ETJ First Impression: T-REX V7.5Dino-Software Introduces T-REX V7.5 Delivering Significant New Enhancements By Denny Yost, ETJ Magazine (5-minute read) Dino-Software continues to excel at taking on and easing the challenge of working with VSAM files and catalogs through its well-known and highly popular T-REX product. T-REX is a proven mainframe utility that analyzes, diagnoses, reorganizes, reports, backs up and repairs clusters while also assisting with the overall maintenance to ensure continuous operational capabilities of the ICF catalog components in a z/OS environment. For many years, T-REX has aided in the monitoring and maintenance of catalog and cluster health to minimize this tedious and time-consuming task. T-REX continues to provide invaluable assistance to those professionals tasked with ensuring the ICF environment and VSAM clusters... Read More |
Catalog Basics - VVDSBy Blair Svihra, Dino-Software (10-minute read) *Restricted Member Content* An ICF catalog is comprised of two entities: the Basic Catalog Structure (BCS) and the VSAM Volume Data Set (VVDS). Up until DFP 3, the VVDS was strictly used as a repository for describing the VSAM data sets physically residing on the volume with the VVDS. Variable length records residing in the VVDS, not the BCS, contain the critical information describing each VSAM entity such as extent information,... Read More |
|
 | ETJ First Impression: T-REX V7.4New T-REX V 7.4 From Dino-Software Delivers Added Functionality By Denny Yost, ETJ Magazine (5-minute read) After working awhile with ICF catalogs and VSAM clusters, it probably reminds you of playing the arcade game Whac-A-Mole. Just when you think everything is under control, some other problems appear. Dino-Software continues to excel at taking on and easing the challenge of working with VSAM files and catalogs through its T-REX product solution. T-REX is a proven mainframe utility that analyzes, diagnoses, reorganizes, reports, backs up and repairs clusters and assists with overall.... Read More |
(Updated) Mysteries of Buffer Optimization Solved!By Bill Hitefield, Dino-Software (12-minute read) |
|
 | ETJ First Impression: HSM Adminisaurus V3.2New HSM Adminisaurus V3.2 From Dino-Software Eases Wrestling with HSM By Denny Yost, ETJ Magazine (5-minute read) Wrestling with DFSMShsm (HSM) to keep it properly managed is no easy task. Under ordinary circumstances, understanding what HSM is doing and monitoring the health of the HSM environment is tedious … at best. Administrators require years of experience in storage management with HSM before they can somewhat manage it. To interpret what functions of HSM are executing successfully takes hours of work if you are lucky and days for those not so lucky. Dino-Software has taken on the challenge of wrestling with DFSMShsm by taming it with HSM Adminisaurus (HSA). HSA greatly simplifies managing HSM by providing over 30 pre-established... Read More |
Catalog Basics - SMF Forward RecoveryBy Blair Svihra, Dino-Software (10-minute read) *Restricted Member Content* When ICF catalogs were first introduced in the early 1980’s, Integrated Catalog Facility Recovery Unit (ICFRU) was IBM’s recommended tool to recover a damaged catalog. An Access Method Services EXPORT of the broken catalog was required as the starting point for the recovery. Snapshots of catalog records, in the form of SMF records, are applied to the EXPORT to “up-level” the catalog to create a new “recovered” EXPORT copy. ICFRU provides no support for the recovery of a VVDS. This whitepaper discusses the use of SMF data for Integrated Catalog Facility (ICF) catalog recovery and its complexities. Read More |
|
Catalog Basics - (BCS) Basic Catalog StructureBy Blair Svihra, Dino-Software (10-minute read) *Restricted Member Content* The BCS, or Basic Catalog Structure, is primarily used as a data set locator. Vital data set information (AMDSB information, extent information, data set attributes and so on) is in the VTOC (Volume Table of Contents) and the VVDS (VSAM Volume Data Set) on the DASD volume where the data set resides. BCS information includes the data set name, volser and device type where the entry physically resides, ownership information, data set security information (if applicable) and possible VVDS and VTOC RBA (relative byte address) pointers. To facilitate quicker access to the components on a volume,... Read More |
|
 | Introduction to Concurrent Copy -By Jim Ratliff, Dino-Software (12-minute read) Concurrent Copy is the IBM solution that allows data to be copied or dumped while it is still active. To utilize Concurrent Copy (CC), you must have the feature activated on the Control Unit that contains your data. Concurrent Copy may be used for Backup, Copy or Dump operations from either DFSMShsm (DFHSM), DFSMSdss (DFDSS), or both. Data may be identified by individual dataset name or volume serial number. In either case, once the data is identified, Concurrent Copy will process the data by protecting and copying tracks. This means if a dataset has a single 80-byte record on a given track, the entire track is identified and processed. There is no record level processing in Concurrent Copy. There are many references in the IBM DFSMS publications identifying how to use CC; therefore, this paper gives an overview of the resources being utilized so the user gains a better understanding of why CC is more complex than often realized. After reading and understanding this information, you should be able to define your Concurrent Copy data and initiate Concurrent Copy with a higher success rate than you may have obtained in the past. Read More |
Realities & Limitations of z/OS SRM Tools - Part 1By Dino-Software (10-minute read) *Restricted Member Content* Management of data on z/OS Systems is complex. A handful of software programs are available, but are they really a “tool?” Do they simplify or complicate? Do they contribute to savings or drive up cost of operations? Often, more time, money, and resources are spent on installation, configuration, customization, training, and the subsequent cumbersome maintenance of the altered product; this ultimately adds up to the overall cost outweighing the intended benefit. This article is Part 1 in a series which explores what your storage team needs to know about z/OS Storage Resource Management (SRM) solutions. Read More |
|
 | The Need For Erase |
 | ETJ First Impression: VR 5.1VELOCI-Raptor Release 5.1 – Enabling Applications to Perform at Their Peak By Denny Yost, ETJ Magazine (5-minute read) With a significant percent of Fortune 500 size organization’s running on mainframe systems, their value and importance are critical to the continued success of the enterprise. Yet, running these applications in the most efficient manner possible to speed execution time and minimize resource usage continues to be challenging if the proper steps are not taken. A key area of focus is always determining and setting the best buffering environment for an application when accessing VSAM and non-VSAM data. Read More |
ETJ First Impression: UDMReduces Costs, Eases Storage Management Through a Single Pane of GlassBy Denny Yost, ETJ Magazine (5-minute read) The Challenges – Today, most Fortune 500 size companies have an abundance of mission-critical data to manage that continues to grow at a seemingly never-ending pace. At the same time, z/OS storage management personnel with decades of experience are retiring and less experienced personnel are agonizing under the load of trying to manage this data while attempting to quickly gain the vast experience needed to manage these environments. Read more . . . |
|
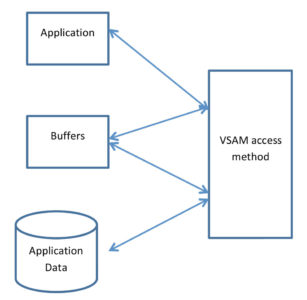 | Mysteries of Buffer Optimization Solved!A Good Buffering Product Does It Automatically – and Does It All the TimeBy Bill Hitefield, Dino-Software (12-minute read) In some respects, IBM’s access methods (especially VSAM) are like software black boxes – you pass a request to them, they go off into the Enchanted Forest, and sometime later, data is either retrieved or written by your application. As application developers, we have some modicum of control over when, why, and how often we make requests to the access method. It is that second part of the process, the “sometime later,” that we view as a part of application performance that we seemingly have no means of influencing. Read More . . . |


